Introduction
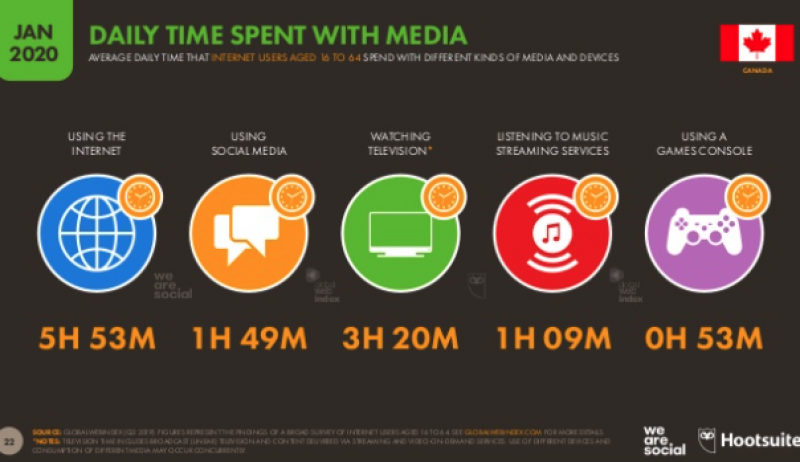
The internet has come a long way since it was first developed in the late 1960’s as a tool for supercomputers to communicate. Today, virtually every aspect of our daily lives is touched in some way by the connected online tools that help people communicate, read the news, shop, play games, watch videos and provide many other services. Canadians spend nearly six hours every day online and throughout that time we are all interacting with tools and systems that gather, process and share our data.
The sharing of our data is the price of admission to access the tools and devices that help simplify our daily lives. With all of this ‘information’ being transferred, such as our habits, preferences, routines, and other personal information, we often forget that vulnerabilities exist in the network due to the accumulation of information we eventually cannot monitor, manage and control. Many technologies we use at work and home are not intended for secure communications, and it is imperative that we take every precaution reasonable to protect ourselves from threat actors who take advantage of security weaknesses.
“It takes 20 years to build a reputation and few minutes of cyber-incident to ruin it.”
-Stephane Nappo
Why Data Security Matters
According to McAfee – a leader in cyber security, in 2020 there have been more than 375 new threats per minute from online criminals trying to harvest user data via malicious apps, phishing campaigns, malware, and more. Many of these attacks are directed at small to medium-sized businesses (SMBs) and non-profits who often lack the sophisticated cybersecurity measures of large corporations but possess valuable digital assets. A data security breach can be a major headache for both companies and individuals with significant financial implications. According to IBM the average cost of a company’s data breach is $3.8M USD. Additionally, data breaches have a lasting impact on a company’s brand. The Ponemon Institute study showed that 65% of consumers who experienced a data breach lost trust in the company and 27% stopped doing business with them altogether. The flip-side to all the potential negative impacts of a data breach is to invest in data protections and build trust with your customer. This approach encourages transparency and reduces friction as customers become advocates for your brand. Before we can get into how to protect your company you need to first understand the threats that are out there.A Rise in ‘Threat Actors’
As people spend more time online it’s natural that there will be more attempts to steal their data, assets and money. Those people that use the web for nefarious purposes are called Threat Actors.
A threat actor is an entity that is partially or wholly responsible for attacks that may impact the security of an individual, company, or government. This could include hackers, nation states, hacktivists or others.
What types of information do they want?
Threat actors look for a variety of information and tend to target organizations instead of individuals as the payoff can be much more lucrative.
Common information they may attempt to secure includes:
- Employee information, including home address, phone number, date of birth, etc.
- Product information, including designs, plans, patent applications, source code, and drawings
- Financial information, including market assessments and your company’s financial records
- Customer information, including confidential information you hold on behalf of customers or clients
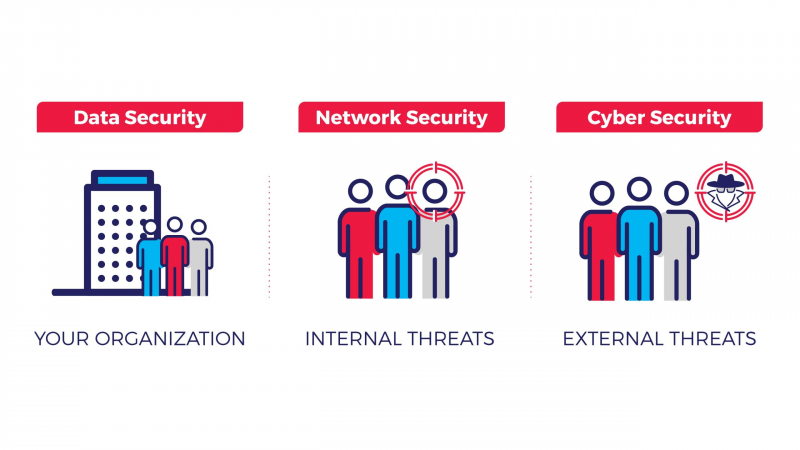
Types of Security
Before developing a security program for your organization to combat against threat actors, it’s critical to understand the different types of security and threats involved.
- Data security
Data security, also known as information security, is an essential aspect of IT for organizations of every size and type. Data security ensures that both physical and digital data is protected from unauthorized access, use, modification, or destruction.
- Cybersecurity
Cybersecurity is a subset of data security that focuses on defending your organization’s networks, computers and data from unauthorized digital access, attack or damage.
Cybersecurity mainly focuses on protecting against external threats and tactics used by threat actors to bypass security systems. Threats are dealt with by implementing various processes, technologies and practices.
Every year, cybersecurity attacks are responsible for causing billions of dollars in losses. These attacks can negatively impact a company’s reputation and put its employee, customer, product, and financial information at risk.
Examples of cyber-attacks:
- Viruses and malware – malicious software designed to cause damage to your computer
- Ransomware – malicious software that can encrypt your files and demand a ransom or payment from you to regain access.
- Worms – similar to a virus by design but can spread between computers without any human action via information transport features on your system.
- Trojan horses – malicious software disguised to appear useful. Trojans are also known to create a backdoor on your computer that allows other threat actors to access your system.
- Zero-day attacks – an attack where the threat actor identifies a flaw in the software, hardware, or firmware that is unknown to the party responsible for fixing the flaw.
- Denial of service attacks – an attack where the threat actor takes action to flood a targets servers, systems or networks with traffic to prevent legitimate users from accessing targeted computer systems.
- Spyware – software that enables a threat actor to obtain personal information about a target’s computer activities.
- Adware – software that automatically displays or downloads unwanted advertising material when a user is online.
Examples of social engineering attacks:
As most organizations have a certain level of protection against cyber threats via antivirus software, threat actors often exploit weaknesses in human psychology through the process of social engineering. In social engineering, threat actors manipulate and trick people into giving them access to sensitive information using a variety of media.
- Phishing – online fraud where targets receive an urgent email that claims to be from a trusted source, such as IT Services. The email may ask targets to validate or confirm certain account information by logging into a fake website often linked to the email.
- Vishing – an alternative to phishing done over the phone or through voice conversation where the threat actor pretends to be from a bank, police station, etc.
- Smishing – another alternative to phishing done through SMS and text messaging urging the target to call a certain number.
- Pretexting – unlike phishing where urgency or fear is communicated, pretexting is when threat actors impersonate an authority figure to build a false sense of trust with the target.
- Email Spam – unsolicited email that can lead to phishing websites or sites that are hosting malicious software.
- Baiting – an online and physical social engineering attack that promises the victim a reward.
- Quid pro quo – when a threat actor bribes targets with money, gifts, etc. in exchange for personal information.
- Tailgating – when a threat actor follows a target into a restricted area to gain access to sensitive information stored in the company office.
The common thread in all of these techniques is the human element. Threat Actors will take advantage of human emotions and response to steal what they want.
Network security
Network security is a subset of cybersecurity that aims to protect any data that is being sent through devices in your network to ensure that the information is not changed or intercepted. Unlike cybersecurity that looks primarily at external threats, network security primarily looks at ways of protecting internal information from within, such as monitoring employee and network behaviour through the following:
- ID and Password – ensuring employee passwords are effective and updated frequently
- Firewalls – keeping outside threats at bay
- Internet access – monitoring the sites employees visit
- Encryption – encrypting company information so that it is useless to anyone outside the company
- Backups – scheduling regular backups of company
- Scans – conducting regular virus and malware scans to detect any outside infection
A common approach by information security experts is to use the CIA triad framework, composed of the principles of confidentiality, integrity, and availability, as a guide to developing policies and procedures for an effective data security program. The CIA triad framework is the standard model for keeping organizations secure.
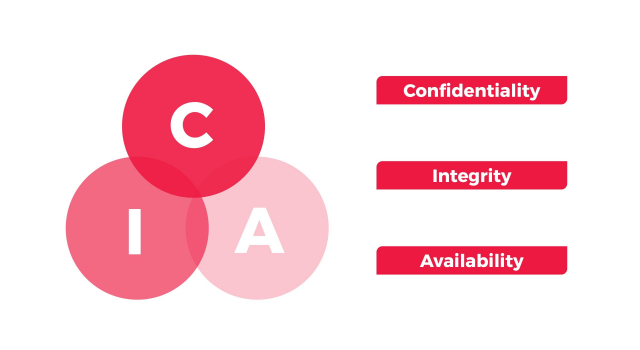
The components of the CIA triad are:
- Confidentiality – ensures information is accessed or read by only authorized users.
- Some examples of common enforcement tools include encryption, user ID’s and passwords, access control lists (ACL) and policy-based security.
- To prevent internal conflict, users shouldn’t be able to ‘read up’ if their classification is below that of the information they are trying to access. For example, if a user has secret classification, he or she can’t read top secret classified material, but can read material classified below that.
- Integrity – assures that data or information systems is accurate and can be trusted and free from modifications by unauthorized people.
- Data encryption and hashing algorithms are key processes in providing integrity.
- To prevent internal conflict, users shouldn’t be able to ‘write down’. For example, if a user has top secret classification, he or she can modify top secret material, but cannot modify secret or public material. This guarantees that there is no accidental leakage of information to lower classified material.
- Availability – ensures authorized people can access data and information systems when needed. To do this, hardware and software are maintained properly and updated when necessary to avoid disruption from threat actors.
Data security boils down to two questions:
- Who is the user?
- What should the user have access to?
The purpose of a data security program is to differentiate between right and wrong users by using the following authentication methods:
- ‘What you know’ authentication – knowledge of secret information known only to the real user and computer. For example, a username and password. This is the easiest security system to put in place.
- ‘What you have’ authentication – based on possession of a secret token or authenticator that the real user has. For example, an id card that grants the user access to an office building, or a text message sent only to your smartphone.
- ‘What you are’ authentication – based on characteristics unique to the real user that he or she presents to the device. For example, biometric login devices that require your unique fingerprint.
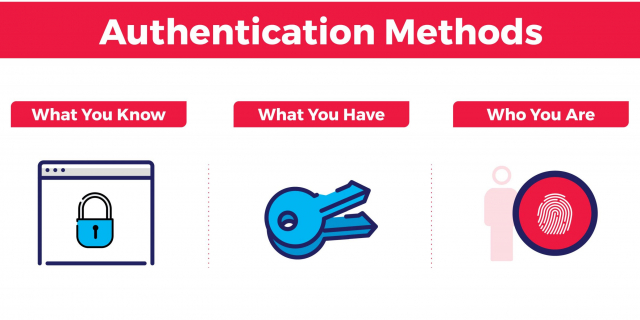
The first two authentication methods are commonly used due to their deterministic nature where the result is either correct or incorrect. ‘What you are’ authentication is a bit more difficult to implement given its probabilistic nature.
There is a chance that probabilistic authentication, such as iris scanning, won’t get recognized. Furthermore, ‘what you are’ authentication cannot be reset, meaning that if a threat actor can get a hold of an exact copy of your iris or fingerprint, there is no way of protecting sensitive information.
Threat actors may be able to get a hold of your username and password; however, if an organization introduces two factor or multifactor authentication, it is unlikely that threat actors can successfully obtain the sensitive information they are looking for.
Data Security Best Practices
Social engineering cyber-breaches often happen because of the human instinct of trust. Threat Actors have gradually tested and enhanced their approaches to create expertly crafted emails, voicemails, or text messages that convince people to transfer money, provide confidential information, or download a file that installs malware on the company network.

To avoid being duped by a Threat Actor companies should follow these simple rules:
- Follow policies: The organization should establish, implement and maintain the policies about data security. Policies such as security awareness, virus protection, visitor access should be made available to all employees and enforced. The organization should review the policy on a regular basis to meet the demands of the organization’s security requirement and to keep up to date with emerging security threats.
- Promote a culture around data security: Threat actors know that the weakest link in most organizations’ security is the human factor, not technology. Every employee, regardless of if the employee has access to a computer or not, is responsible for protecting against social engineering attacks. Employees should be aware of the risks that come with the use of technology and not assume that there is an instant fix to problems they may face.
- Encourage employees to create a strong password: Creating a secure password is an important part of keeping your personal information safe, protecting your emails, files, and other content, and prevent threat actors from breaking into your account.
A strong password is nearly impossible for someone else to guess and requires threat actors to spend more effort and time to guess. Here are some tips for creating a good password:
Passwords must be long and complex (10+ characters with letters, symbols, numbers, etc.)
- Don’t make a password too personal
- Change your password regularly
- Never use the same password for two or more devices
- Never write down passwords
- Think beyond data theft: Organizations often forget that there are internal threats that could put the company’s data at risk. This includes losing data due to not backing up equipment, human error caused by employees or third-parties, and blackouts at data centres. It’s important that every organization has a disaster recovery plan to ensure business continuity in the event of temporary data loss.
- Regular tests and modifications: Organizations with few or no data breaches still need to be aware that their security program can be further improved. The technology and policies in place should be regularly tested and assessed by professional security organizations that can identify areas of weakness.
Important: If your organization experiences a data breach, consult the Government data breach guidelines in Canada , the United States or other countries where users may be effected.
Summary
Protecting your organization’s data is becoming increasingly difficult with the rise of data-driven decision making and data gathering devices. Data security is now more important than ever as threat actors are finding more uses for your organization’s physical and digital data, regardless of the industry or line of business you are in. To ensure that your organization doesn’t fall victim to a data breach, it’s important to understand current cyber and network security risks, and what can be done to protect against them.
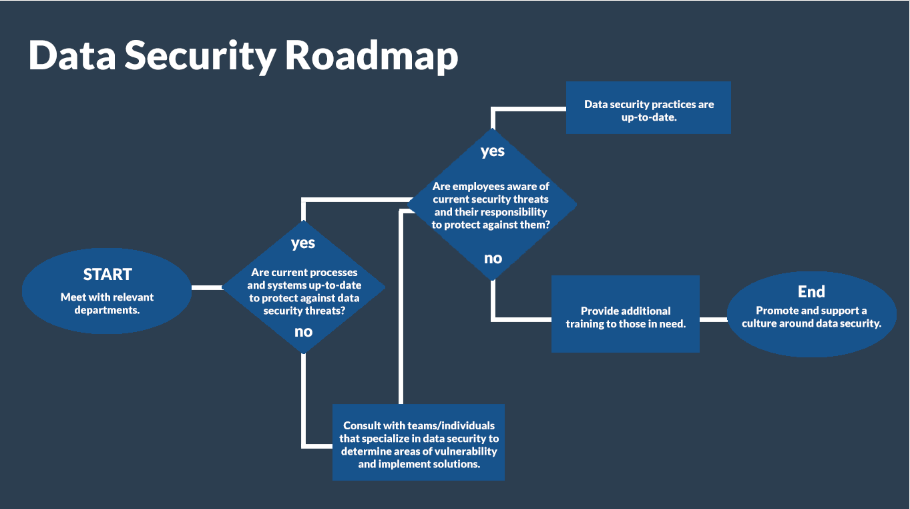
To better protect your organization from data security threats, refer to the roadmap below for next steps.